Cross-Site Scripting (XSS)
Cross-site scripting (XSS) is a security vulnerability that allows hackers to inject malicious JavaScript into vulnerable websites which then sends it to its users. When the malicious JS is executed by users in their browsers, the script can access sensitive user data and take actions on the site on user’s behalf. This is because user’s browser has no way of knowing that the script is untrustworthy so it gives it complete access to cookies, session tokens, and other sensitive information that user has access to on that site.
It’s is important to note that XSS attacks only expose user information on the website that’s compromised and doesn’t affect other websites. For example, suppose there’s an XSS script on “youtube.com”. It will give hackers access to all of user’s data on Microsoft but not on other sites like “hbomax.com” or “disney.com”, etc.
How does XSS Work?
Suppose there’s a vulnerable video hosting website that allows users to comment on videos. The website doesn’t sanitize user input in comments and hence is vulnerable to XSS. A hacker injects malicious JavaScript into the site masquerading as a comment:
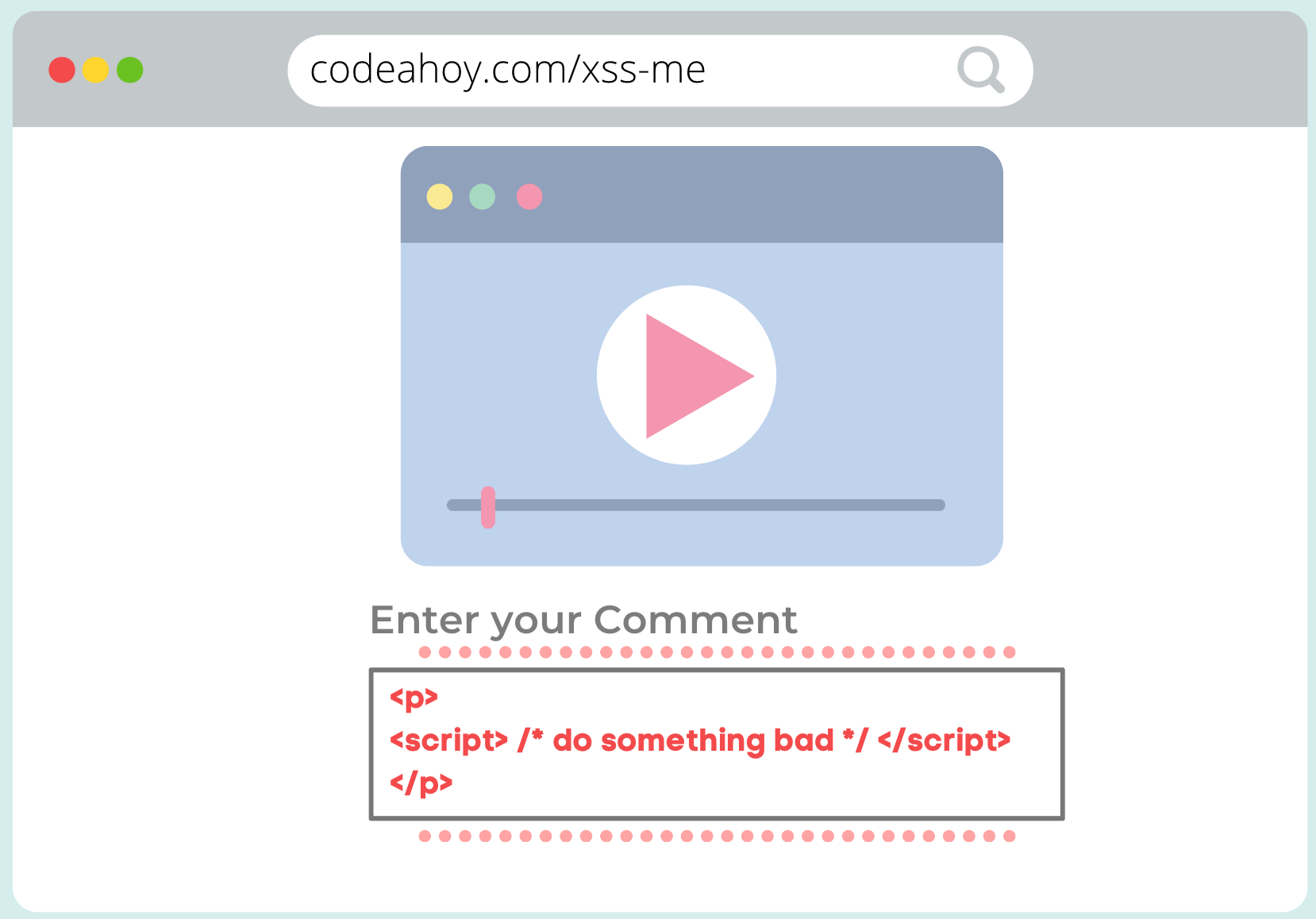
Hacker injecting JavaScript using a vulnerable website’s comment section.
The JavaScript that hacker injecting will be stored on the server and will be sent to all users who view this web page. The JavaScript will be executed in user browsers just like any other JavaScript from the site and will have access to all user actions. It can do something mild like “up vote” hacker’s videos to something serious like stealing user’s credentials and sending them to hacker’s servers.
Types of XSS
There are three main types of XSS attacks:
- Stored XSS
- Reflected XSS
- DOM-based XSS
1. Stored XSS
In Stored XSS attacks, the malicious script is injected into a website and is stored on target servers. The users get this script without even knowing when they access the page. The example we saw above describes Stored XSS attack.
2. Reflected XSS
In Reflected XSS attacks, the victim is tricked into opening a link with malicious code that the vulnerable websites executes. For examples:
https://codeahoy.com/xss-me?comment=<script>DoSomethingBad</script>
If the user visits the URL sent by hacker and the website has XSS vulnerability, the hacker’s script will execute in user’s browsers and has full access to everything on the site that user has access to.
3. DOM-based XSS
This is the least common type of XSS attack. In DOM based XSS attacks, when an web page executes a JavaScript from an unsafe source and executes it without validating. Here, the actual webpage (server response) doesn’t change, but the malicious client side code is executed by browser modifying DOM. An example would be a webpage asking for user’s input and then displaying that input on the page by writing to DOM.
var firstName = document.getElementById('fname').value
var lastName = document.getElementById('lname').value
var name = document.getElementById('fullName');
name.innerHTML = 'Your name is ' + firstName + ' ' + lastName;
An attacker can easily run malicious code to run their own script:
Your name is <script>DoSomethingBad</script>
How to protect against XSS
XSS attacks only work if the website doesn’t validate its input. For large websites, it can be quite a big undertaking to find and resolve all XSS vulnerabilities. To prevent XSS, it’s a combination of the following methods:
- Sanitize and filter all user input. Encode the data using combination of HTML, JavaScript and CSS encoding.
- Use the
Content-TypeandX-Content-Type-Optionsheaders. - Use Content Security Policy .
(C) 2021 CodeAhoy.com. You can use the material on your site but you must link back to this page.