
HTTPS (aka HTTP over the secure TLS protocol) provide a secure communication channel between web browsers and servers to guard against man-in-the-middle attacks. Although researchers have identified and reported a few vulnerabilities, TLS is still the best option out there and all websites should be using it.
Arguably, the most famous TLS fiasco was not a vulnerability but an enormously miscalculated and incompetent attempt to increase ad revenues by a top selling laptop manufacturer. “Lenovo incident / scandal” got its start when Lenovo thought it would be a brilliant idea to pre-install an adware (Superfish) on their laptops to inject ads on webpages, both encrypted and non-encrypted. To allow Superfish to view and alter encrypted traffic, they pre-loaded its self-signed, root certificate on their laptops. By doing this, Lenovo let Superfish become man-in-the-middle and allowed it to view and alter traffic without the user ever knowing. If that was the end of the story, it might not have been all that terrible. However, by installing the self-signed root certificate, which used the same private key on all laptops, Lenovo exposed sensitive and confidential communication of their users to attackers or eavesdroppers connected to the same WiFi. Communication including emails, bank transactions, messages, and passwords were all exposed. After users complained and there was public outcry, Lenovo finally acknowledged that it “messed up” and apologized to users for betraying their trust. It quickly dumped Superfish. Microsoft stepped in and provided an update of Windows Defender to remove Superfish.
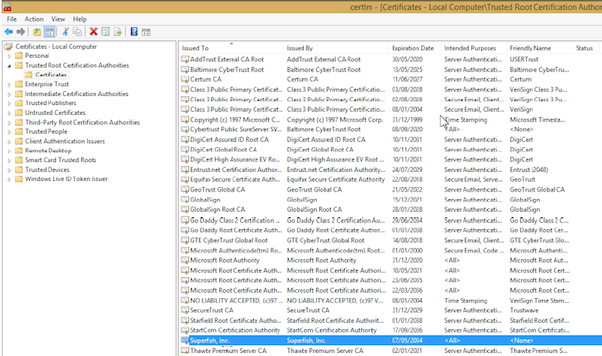
As someone who purchased a Y50 around the same time (2014), I’m happy to report that Superfish is dead. (So long, and no-thanks for the fish.)
It is not always the incompetence of laptop vendors - user trust has been violated intentionally for malicious purposes as well:
a Chinese certificate authority issued valid security certificates for a number of domains, including Google’s, without their permission, which resulted in a major trust breach in the crypto chain.
CNNIC had delegated its authority to Egyptian intermediary MCS Holdings to issue the certificates in question and the company installed it in a man-in-the-middle proxy internally.
If China feels far away, Symantec fired its employees after it discovered they issued fake google security certificates.
As a user, you can protect your communication and your privacy by never ignoring security warnings from your web browser. Web browsers, especially Chrome and Firefox, do a pretty good job of recognizing potential threats and warning users, so don’t skip through unless you are absolutely sure what you are doing. They also have a “Removal of Trust“ policy where they would distrust a root certificate authority if it is compromised, even if it is trusted by the operating system.
See you next time!